The NCCC at the NSDC of Ukraine warns of high level of cyber threats due to the exploitation of vulnerabilities in Microsoft Exchange
The National Coordination Center for Cybersecurity at the National Security and Defense Council of Ukraine warns of the active exploitation of vulnerabilities in the widespread software product Microsoft Exchange. If the vulnerabilities are successfully exploited, attackers can execute arbitrary code on vulnerable systems and gain full access to the compromised server, including access to files, e-mail, accounts, etc. Moreover, the successful exploitation of vulnerabilities allows unauthorized access to the resources of the organization’s internal network.
Local versions of Microsoft Exchange Server 2010, Microsoft Exchange Server 2013, Microsoft Exchange Server 2016, Microsoft Exchange Server 2019 are vulnerable. There is no information on vulnerabilities in cloud versions of Microsoft 365, Exchange Online, Azure Cloud.
Vulnerabilities CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065 (common name – ProxyLogon) are currently actively exploited, for vulnerabilities CVE-2021-26412, CVE-2021-26854, CVE- 2021-27078 there are no publicly available exploits.
The greatest activity in exploiting vulnerable systems was demonstrated by the Chinese cyber espionage group Hafnium, but now the activity of other hacker groups has been also confirmed, including Tick (Bronze Butler), LuckyMouse (APT27), Calypso, Websiic, Winnti Group (BARIUM, APT41), Tonto (CactusPete), ShadowPad, Microceen, DLTMiner.
The vulnerability is exploited not only by intelligence groups but also by cybercriminals. The facts of infecting vulnerable systems by ransomware, in particular, new families DearCry, DoejoCrypt have been confirmed. Ransom demanded by the criminals in one of the confirmed cases amounted to over 16 thousand dollars.
Compromised servers are also used to send malware to further infect as many organizations as possible. Several such incidents have already been reported in Ukraine.
It should be noted that usually after compromising the next phases are intelligence (data collection on information systems), and afterwards – information theft. This takes some time, and then in many cases valuable data is encrypted or deleted, and ransom is demanded for them. Such a mechanism for developing cyberattacks poses significant threats of data loss in compromised organizations in the near future – from weeks to months.
Microsoft has released service packs for vulnerable versions and software tools designed to self-test for vulnerabilities (https://github.com/microsoft/CSS-Exchange/tree/main/Security). According to the analysis of update settings and partner notifications, the update procedure does not always automatically provide protection against vulnerabilities for all minor versions of Microsoft Exchange Server. For example, according to the Norwegian parliament, their information systems were hacked and data stolen, although updates had been installed.
Therefore, when installing service packs one should consider the following. The update must be applied from the command line on behalf of a user with administrator privileges, after the installation the server must be restarted. After the update process is complete, the vulnerability must be re-examined (MSERT tool – https://docs.microsoft.com/en-us/windows/security/threat-protection/intelligence/safety-scanner-download or nmap https://github.com/GossiTheDog/scanning/blob/main/http-vuln-exchange.nse script).
Earlier, Microsoft reported unauthorized access to fragments of the source code of its products during a large-scale cyberattack on government agencies and private organizations in the United States, called Solorigate. It is reported that some of the identified vulnerabilities were exploited (as zero-day vulnerabilities) at least 2 months before the release of service packs for Microsoft Exchange Server.
Therefore, the NCCC recommends that vulnerable versions of Microsoft Exchange Server and the networks in which they are used be considered compromised and that incident response procedures be used. If the fact of compromise is not confirmed during the response, it is recommended to strengthen security monitoring measures and monitor the situation, as new data on tactics, techniques and procedures of attackers are received, and indicators of compromise are updated.
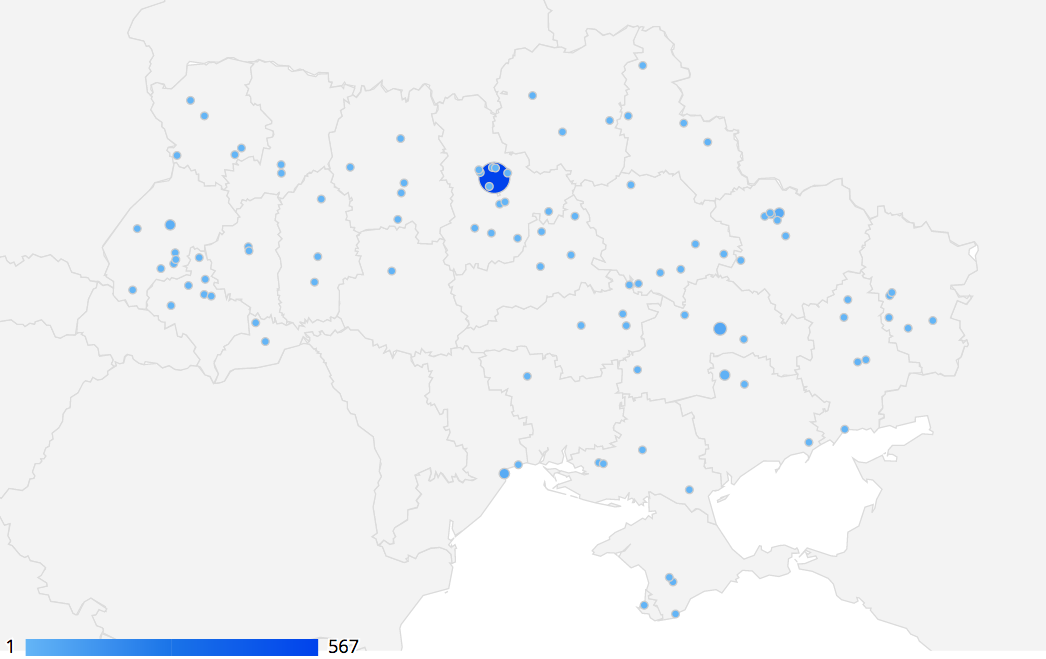
As of March 12, 2021, more than 1000 vulnerable Microsoft Exchange Server servers were identified in Ukraine, of which 98,7% are used in the private sector.
The NCCC encourages immediate reporting of compromises or attempts to exploit vulnerabilities at report@ncscc.gov.ua for a coordinated response. The NCCC experts are ready to provide technical and advisory assistance in responding, in particular, to private sector organizations.
The geographical distribution of vulnerable servers is shown in the figure.
Technical data
The CISA (US) agency recommends searching for signs of compromise at least from January 1, 2021.
You can check for signs of compromise by running the script (Microsoft) Test-ProxyLogon.ps1 (https://github.com/microsoft/CSS-Exchange/tree/main/Security)
During the exploitation of vulnerabilities in the compromised system, a so-called web shell – a script designed for remote access and management (administration) of an infected system. Typically, a web shell is used to steal credentials, download other malicious code (for example, to search for other victims and infect them), as a command server to manage other infected systems.
Volexity has analyzed the exploitation of Microsoft Exchange Server vulnerabilities. According to the analysis:
HTTP POST requests are made to the following files:
/owa/auth/Current/themes/resources/logon.css
/owa/auth/Current/themes/resources/owafont_ja.css
/owa/auth/Current/themes/resources/lgnbotl.gif
/owa/auth/Current/themes/resources/owafont_ko.css
/owa/auth/Current/themes/resources/SegoeUI-SemiBold.eot
/owa/auth/Current/themes/resources/SegoeUI-SemiLight.ttf
/owa/auth/Current/themes/resources/lgnbotl.gif
ESR server log files in \Logging\ECP\Server\ contain the following or similar strings:
S:CMD=Set-OabVirtualDirectory.ExternalUrl='
The presence of files in the following directories indicates an active web shell:
\inetpub\wwwroot\aspnet_client\ (any.aspx file in this directory or in subdirectories)
\\FrontEnd\HttpProxy\ecp\auth\ (any.aspx file except TimeoutLogoff.aspx)
\\FrontEnd\HttpProxy\owa\auth\ (any file or modified file that is not part of the standard installation)
\\FrontEnd\HttpProxy\owa\auth\Current\ (any.aspx file in this directory or in subdirectories)
\\FrontEnd\HttpProxy\owa\auth\\ (any.aspx file in this directory or in subdirectories)
A directory search by /owa/ auth/Current contains the following user-agent strings:
DuckDuckBot/1.0;+(+http://duckduckgo.com/duckduckbot.html)
facebookexternalhit/1.1+(+http://www.facebook.com/externalhit_uatext.php)
Mozilla/5.0+(compatible;+Baiduspider/2.0;++http://www.baidu.com/search/spider.html)
Mozilla/5.0+(compatible;+Bingbot/2.0;++http://www.bing.com/bingbot.htm)
Mozilla/5.0+(compatible;+Googlebot/2.1;++http://www.google.com/bot.html
Mozilla/5.0+(compatible;+Konqueror/3.5;+Linux)+KHTML/3.5.5+(like+Gecko)+(Exabot-Thumbnails)
Mozilla/5.0+(compatible;+Yahoo!+Slurp;+http://help.yahoo.com/help/us/ysearch/slurp)
Mozilla/5.0+(compatible;+YandexBot/3.0;++http://yandex.com/bots)
Mozilla/5.0+(X11;+Linux+x86_64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/51.0.2704.103+Safari/537.36
The above user-agent stings are not mandatory indicators of compromise, but should be investigated further.
Such user-agent strings were observed during the exploit from URL /ecp/:
ExchangeServicesClient/0.0.0.0
python-requests/2.19.1
python-requests/2.25.1
Such user-agent strings were observed after the exploit when accessing the web shell:
antSword/v2.1
Googlebot/2.1+(+http://www.googlebot.com/bot.html)
Mozilla/5.0+(compatible;+Baiduspider/2.0;++http://www.baidu.com/search/spider.html)
If you find non-standard user-agent strings, you must examine the IIS logs on the Exchange server to analyze their activity. The following requests are not mandatory indicators of compromise:
POST /owa/auth/Current/
POST /ecp/default.flt
POST /ecp/main.css
POST /ecp/.js
According to Microsoft, there was a web shell in the following directories:
\inetpub\wwwroot\aspnet_client\
\inetpub\wwwroot\aspnet_client\system_web\
%PROGRAMFILES%\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\
\Exchange\FrontEnd\HttpProxy\owa\auth\
File names of detected web shells:
web.aspx, help.aspx, document.aspx, errorEE.aspx, errorEEE.aspx, errorEW.aspx, errorFF.aspx, healthcheck.aspx, aspnet_www.aspx, aspnet_client.aspx, xx.aspx, shell.aspx, aspnet_iisstart.aspx, one.aspx
Додатковими індикаторами компрометації можуть бути наявність нестандартних підозрілих архівів .zip, .rar, .7z в каталозі C:\ProgramData\, що може свідчити про витік інформації, та дампів процесу LSASS в каталогах C:\windows\temp\, C:\root\.
Additional indicators of compromise may be the presence of non-standard suspicious archives .zip, .rar, .7z in the directory C:\ ProgramData\, which may indicate a leak, and dumps of the LSASS process in the directories C:\windows\temp\, C:\ root\.
Available indicators
|
File name |
File size |
Hash sum SHA2 |
|
zXkZu6bn.aspx |
2287 |
71ff78f43c60a61566dac1a923557670e5e832c4adfe5efb91cac7d8386b70e0 |
|
shell.aspx |
2287 |
ee883200fb1c58d22e6c642808d651103ae09c1cea270ab0dc4ed7761cb87368 |
|
RedirSuiteServerProxy.aspx |
3349 |
c8a7b5ffcf23c7a334bb093dda19635ec06ca81f6196325bb2d811716c90f3c5 |
|
discover.aspx |
2230 |
1e0803ffc283dd04279bf3351b92614325e643564ed5b4004985eb0486bf44ee |
|
F48zhi6U.aspx |
2211 |
d9c75da893975415663c4f334d2ad292e6001116d829863ab572c311e7edea77 |
|
discover.aspx |
2204 |
c0caa9be0c1d825a8af029cc07207f2e2887fce4637a3d8498692d37a52b4014 |
|
Fc1b3WDP.aspx |
2230 |
be17c38d0231ad593662f3b2c664b203e5de9446e858b7374864430e15fbf22d |
|
UwSPMsFi.aspx |
2168 |
d637b9a4477778a2e32a22027a86d783e1511e999993aad7dca9b7b1b62250b8 |
|
2XJHwN19.aspx |
2177 |
31a750f8dbdd5bd608cfec4218ccb5a3842821f7d03d0cff9128ad00a691f4bd |
|
E3MsTjP8.aspx |
2353 |
bda1b5b349bfc15b20c3c9cbfabd7ae8473cee8d000045f78ca379a629d97a61 |
|
web.config.aspx |
2241 |
5ac7dec465b3a532d401afe83f40d336ffc599643501a40d95aa886c436bfc0f |
|
0q1iS7mn.aspx |
2267 |
138f0a63c9a69b35195c49189837e899433b451f98ff72c515133d396d515659 |
|
McYhCzdb.aspx |
2264 |
0c5fd2b5d1bfe5ffca2784541c9ce2ad3d22a9cb64d941a8439ec1b2a411f7f8 |
|
8aUco9ZK.aspx |
2267 |
36149efb63a0100f4fb042ad179945aab1939bcbf8b337ab08b62083c38642ac |
|
ogu7zFil.aspx |
2284 |
508ac97ea751daebe8a99fa915144036369fc9e831697731bf57c07f32db01e8 |
|
|
|
b75f163ca9b9240bf4b37ad92bc7556b40a17e27c2b8ed5c8991385fe07d17d0 |
|
|
|
097549cf7d0f76f0d99edf8b2d91c60977fd6a96e4b8c3c94b0b1733dc026d3e |
|
|
|
2b6f1ebb2208e93ade4a6424555d6a8341fd6d9f60c25e44afe11008f5c1aad1 |
|
|
|
65149e036fff06026d80ac9ad4d156332822dc93142cf1a122b1841ec8de34b5 |
|
|
|
511df0e2df9bfa5521b588cc4bb5f8c5a321801b803394ebc493db1ef3c78fa1 |
|
|
|
4edc7770464a14f54d17f36dc9d0fe854f68b346b27b35a6f5839adf1f13f8ea |
|
|
|
811157f9c7003ba8d17b45eb3cf09bef2cecd2701cedb675274949296a6a183d |
|
|
|
1631a90eb5395c4e19c7dbcbf611bbe6444ff312eb7937e286e4637cb9e72944 |
ІР addresses
103.77.192.219
104.140.114.110
104.250.191.110
108.61.246.56
149.28.14.163
157.230.221.198
167.99.168.251
185.250.151.72
192.81.208.169
203.160.69.66
211.56.98.146
5.254.43.18
5.2.69.14
80.92.205.81
91.192.103.43
Download in STIX format https://us-cert.cisa.gov/sites/default/files/publications/AA21-062A.stix.xml
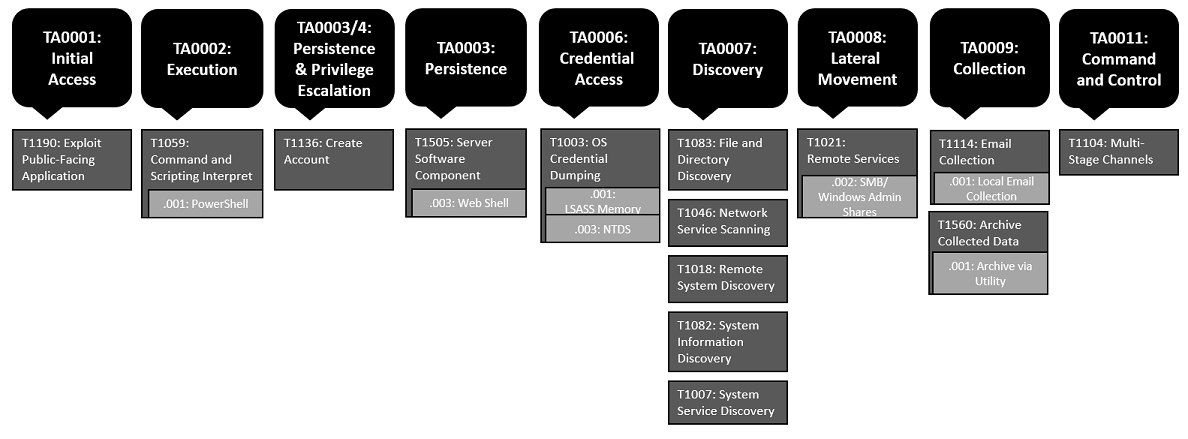
Malicious activities by the MITRE ATT&CK® classification